Encryption on Linux 101
Encryption on Linux 101
Hey there! Welcome to another blog post where we dive into the fascinating world of offensive security and explore the realm of encryption on Linux. In this guide, we’ll walk you through the basics of encryption, discuss its importance, and provide you with some practical tips on how to secure your sensitive data. So grab a cup of coffee, get cozy, and let’s get started!
Why Encryption Matters?
Before we begin, let’s take a moment to understand why encryption is crucial in today’s digital landscape. Encryption is the process of converting plaintext information into an unreadable form, known as ciphertext, using algorithms and cryptographic keys. This ensures that even if an unauthorized person gains access to your data, they won’t be able to decipher it without the encryption key.
Encryption plays a vital role in protecting sensitive information, such as personal documents, financial data, and even your online communications. It adds an extra layer of security and mitigates the risk of data breaches and unauthorized access. With encryption, you can have peace of mind knowing that your confidential data remains secure, even in the event of a security breach.
Encryption on Linux
Linux is renowned for its robust security features, making it a popular choice among security-conscious individuals. When it comes to encryption on Linux, you have several powerful tools at your disposal. Let’s explore some of the key components of encryption on Linux:
1. Filesystem Encryption
Linux offers various filesystem-level encryption options, such as LUKS (Linux Unified Key Setup) and eCryptfs. LUKS is widely used and provides full-disk encryption, ensuring that all data on a particular disk is encrypted. On the other hand, eCryptfs allows you to encrypt individual directories or files. Both options provide strong encryption and are relatively easy to set up.
To encrypt a disk using LUKS, you can use the cryptsetup utility. Here’s an example of the command to encrypt a disk:
$ sudo cryptsetup luksFormat /dev/sdb1
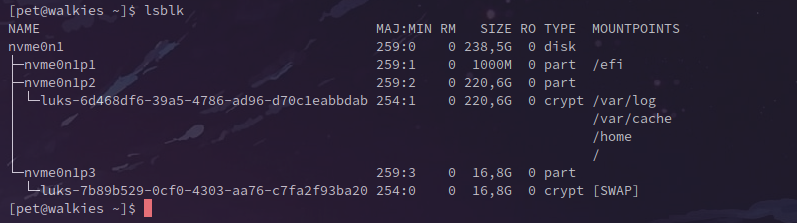
— lsblk of my own encrypted device
Once the disk is encrypted, you can use the cryptsetup luksOpen command to unlock and mount it for use.
2. Secure Communication
Encrypting your communication channels is essential to safeguard sensitive information from prying eyes. Linux offers various tools for secure communication, such as OpenVPN, GnuPG, and SSH. OpenVPN allows you to create secure virtual private networks (VPNs) for secure remote access. GnuPG provides encryption and digital signature functionality, while SSH enables secure remote login and file transfer.
When setting up OpenVPN, it’s important to generate strong cryptographic keys and certificates. Additionally, using SSH key pairs instead of passwords for remote access adds an extra layer of security.
3. Encrypted Email
If you’re concerned about the privacy of your email communications, you can utilize encryption techniques such as Pretty Good Privacy (PGP) or its open-source implementation, GNU Privacy Guard (GPG). These tools enable you to encrypt your emails, ensuring that only the intended recipient can read the contents.
By generating your PGP or GPG key pair and sharing your public key with the recipients, you can establish a secure and private communication channel.
4. Password Management
Keeping your passwords secure is paramount to protecting your online accounts. Linux offers password managers like KeePassXC and Bitwarden, which store your passwords in an encrypted database. These tools help you generate strong, unique passwords and securely manage them without the need to remember them all.
By using a password manager, you can reduce the risk of using weak passwords or reusing passwords across different accounts. These tools also often provide additional features such as auto-fill and browser integration, making the password management process more convenient and efficient.
Best Practices for Encryption on Linux
Now that you’re familiar with the fundamental aspects of encryption on Linux, let’s go through some best practices to enhance your OPSec:
-
Keep Your System Updated: Regularly update your Linux system to ensure you have the latest security patches and bug fixes. This helps protect against known vulnerabilities and keeps your encryption software up to date.
-
Strong Encryption Algorithms: Always use strong encryption algorithms, such as AES (Advanced Encryption Standard) with a key length of 256 bits. These algorithms provide robust protection for your encrypted data. Avoid using outdated or weak algorithms that may be susceptible to attacks.
-
Secure Passwords and Encryption Keys: Use strong, unique passwords for your encryption keys and accounts. Avoid using common or easily guessable passwords. Consider using a password manager to generate and store complex passwords securely. Additionally, protect your encryption keys by storing them in a secure location and using strong passphrase protection.
-
Secure Storage of Encrypted Data: Ensure that the storage devices or mediums where you store your encrypted data are themselves secure. Use reliable and trusted hardware and enable additional security measures, such as BIOS or UEFI passwords, to prevent unauthorized access to your system. Consider using hardware encryption solutions, such as self-encrypting drives (SEDs), for added security.
-
Implement Two-Factor Authentication (2FA): Enable two-factor authentication wherever possible to add an extra layer of security to your accounts. This can help prevent unauthorized access, even if your password is compromised. Linux offers various 2FA solutions, such as Google Authenticator or YubiKey, which can be integrated with SSH or other services.
-
Regularly Back Up Your Data: Implement a robust backup strategy for your encrypted data. Regularly create backups and store them securely in multiple locations, including offsite or cloud storage. This ensures that even if your system is compromised or experiences a failure, you can still recover your important data.
-
Practice Safe Online Behavior: Encryption alone is not sufficient to protect your data if you fall victim to phishing attacks or malware. Be cautious when opening email attachments or clicking on suspicious links. Regularly update and run antivirus software to detect and remove any potential threats.
-
Continuously Educate Yourself: Stay updated with the latest encryption techniques, security best practices, and emerging threats. Attend conferences, participate in security forums, and read reputable sources to expand your knowledge and keep yourself informed about the evolving landscape of encryption and security.
Remember, encryption is just one piece of the security puzzle. It’s essential to adopt a holistic approach to security, including strong passwords, regular updates, and safe online practices, to ensure the protection of your sensitive information.
So there you have it, a basic OPSec guide to encryption on Linux. By implementing these practices and leveraging the powerful encryption tools available, you can strengthen the security of your Linux system and protect your valuable data from unauthorized access.
Stay secure, stay curious, and happy encrypting!